HTTPS
HTTPS is the most common security version for http. Most of commercial
web server and browser provides the
HTTP. Also almost all e-economic websites provides https connections.
HTTPS overview
Here is the architecture of HTTPS. Before sending the HTTP
request to TCP stack, HTTPS will send it to a ‘secure’ layer end encrypted it using
Asymmetric encryption key-pairs.
Typically, https’s url is something like https://websites/, by default the browser will use
port 443 instead of 80. The traffic between your browser and webserver is
binary dataflow and encrypted.
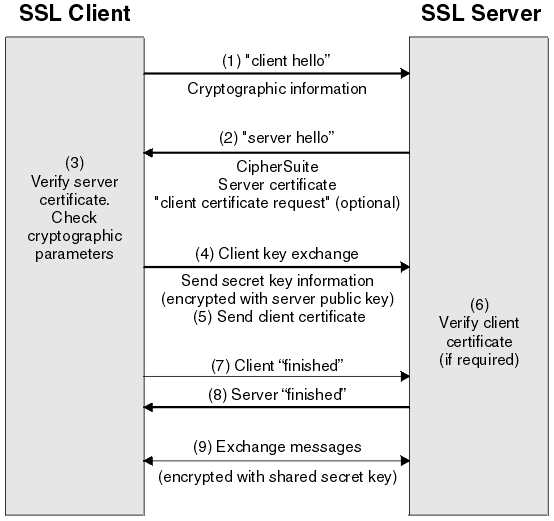
The shakehands processes
(From IBM websites)
- The SSL client sends a "client hello" message that lists cryptographic information such as the SSL version and, in the client's order of preference, the CipherSuites supported by the client. The message also contains a random byte string that is used in subsequent computations. The SSL protocol allows for the "client hello" to include the data compression methods supported by the client, but current SSL implementations do not usually include this provision.
- The SSL server responds with a "server hello" message that contains the CipherSuite chosen by the server from the list provided by the SSL client, the session ID and another random byte string. The SSL server also sends its digital certificate. If the server requires a digital certificate for client authentication, the server sends a "client certificate request" that includes a list of the types of certificates supported and the Distinguished Names of acceptable Certification Authorities (CAs).
- The SSL client verifies the digital signature on the SSL server's digital certificate and checks that the CipherSuite chosen by the server is acceptable.
- The SSL client sends the random byte string that enables both the client and the server to compute the secret key to be used for encrypting subsequent message data. The random byte string itself is encrypted with the server's public key.
- If the SSL server sent a "client certificate request", the SSL client sends a random byte string encrypted with the client's private key, together with the client's digital certificate, or a "no digital certificate alert". This alert is only a warning, but with some implementations the handshake fails if client authentication is mandatory.
- The SSL server verifies the signature on the client certificate. (optional)
- The SSL client sends the SSL server a "finished" message, which is encrypted with the secret key, indicating that the client part of the handshake is complete.
- The SSL server sends the SSL client a "finished" message, which is encrypted with the secret key, indicating that the server part of the handshake is complete.
- For the duration of the SSL session, the SSL server and SSL client can now exchange messages that are symmetrically encrypted with the shared secret key.
Server Digital Certificates
A digital certificate is an electronic "passport"
that allows a person, computer or organization to exchange information securely
over the Internet using the public key infrastructure (PKI). A digital
certificate may also be referred to as a public key certificate. The digital
certificate is issued by a trusted Certification Authority (CA). Server Digital
Certificates are essential for HTTPS communication.
In real world, the server digital certificate is a X.509 v3
electronic copy.
It can be look like:
Usually the client will verify the below items:
- Date: checking if the digital certificates data is expired or not.
- CA: the browser will contain a trusted CA lists. Only the trusted CA’s certificates can be thought as valid.
- Signature: the digital certificate’s checksum should be same as the trusted CA’s signature.
- Domain verification: the digital certification’s websites should be exactly match the website the browser is accessing.



No comments:
Post a Comment