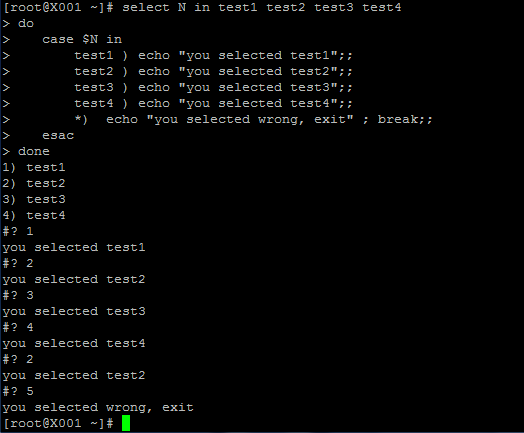
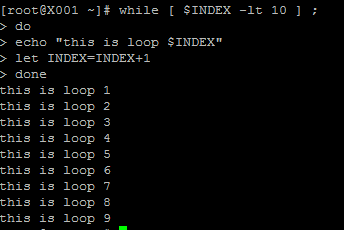
When HTTP was designed, the HTTP client should use different ways to communicate with web server. For example:
- GET for retrieving the information
- POST for updating the information
- PUT for adding the information
- DELETE for deleting the information
But the programmer may do tricky things to use GET to cover the other methods. They could use GET to do data update at the backend. We need to understand what is the difference between GET and POST when updating the data.
- Using GET, the data will be added in the URL as here: login.action?name=hyddd&password=idontknow .While using POST, the data is part of the HTTP content
- Limitation of the data-length. While HTTP itself does not set limitation for URL and web content. Most of the browser will have their limitation.
- Security: the content of GET will be showing in the url which is easier to be seen. Although the transsion traffic can be encrypted by HTTPS. The page could be cached/viewed and can cause security problem.
- Also by theory, GET should be idempotent which means multiple operations should always return the same result.